Active Directory (Single sign on)
This section will introduce the step on how to integrate with Active Directory for single sign on purpose. Based on the following integration steps, user can:
- User can perform single sign on to Bookings ONE system
- User account will be automatically created only when the user first time login, while
Userpermission will be granted
⚠️ The following setting will not sync all user into the system, every user account will be automatically create only when the user first time login to the system. If you want to pre-load all user to the system first, please refer to Active Directory with LDAP User Synchronization
Network Connectivity
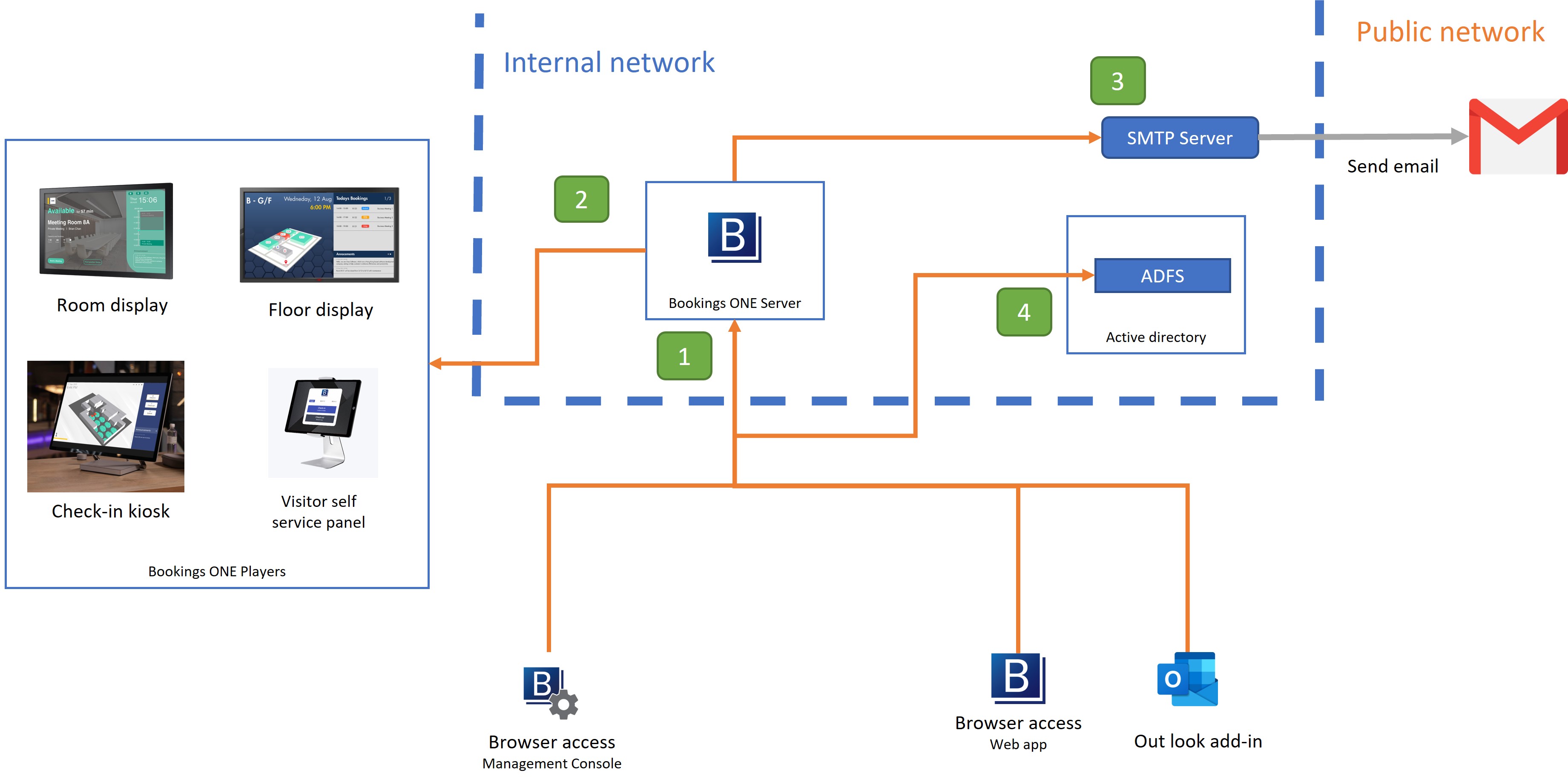
Connect from User Web App, Outlook Add-in, Management Console to Bookings ONE Server
- For open the WebApps of Bookings ONE.
- Port:
TCP 443
Connect from Bookings ONE Server to Bookings ONE Player
- For room display, floor display, etc.. connect to Servers to receive the signal., Bookings ONE Server can real-time update data through the
httpsandwssprotocol. - Port:
TCP 443
- For room display, floor display, etc.. connect to Servers to receive the signal., Bookings ONE Server can real-time update data through the
Connect from Bookings ONE Server to SMTP Server
- For sending email through the SMTP Server, sending email to the receiver.
- Port:
TCP 25, 465, or 587(depend on the SMTP Server setting)
Connect from User Web App, Outlook Add-in, Management Console to the ADFS
- For user single sign on with the Active Directory Federation Services (ADFS)
- Port:
TCP 443
Integration Steps
- Microsoft Active Directory / Azure AD
- Configure the ADFS / Azure active directory. Please follows ADFS setup guide and AzureAD setup guide
- Open
Bookings ONE Management Console - Navigate to
Settings > External Integration - Click
New external integration +button, selectActive Directory (Single sign on) - Fill in the Metadata address and WtRealM
- For Exchange server
- In metadata address, fill in follow address
https://{your active directory address}/FederationMetadata/2007-06/FederationMetadata.xml - In Wt RealM, fill in the for WS-Federation Passive protocol app's URL configured in active directory
- In metadata address, fill in follow address
- For Office 365
- In metadata address, fill in WS-Federation middleware's MetadataAddress
- In Wt RealM, fill in the Application ID URI
- (Optional) Fill in Login button name, it will show
Login via Active directoryif leave the field empty - Click
Savebutton. - Set the redirect URI from the ADFS integration to Azure. Please refer to ADFS setup guide.
- Now user can single sign on in login page

Default login field and buttons are for user to login via system local accounts. If you are using the system without any local user accounts or you do not want user to login via local account, you can hide these fields by following steps in Management Console:
- Navigate to
Settings > General - Select
Hidden local login in User App - Click the
Updatebutton